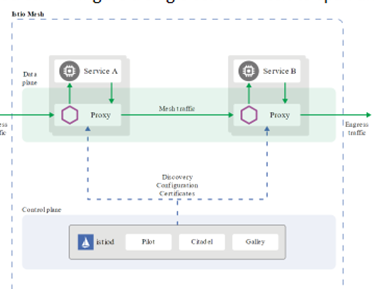
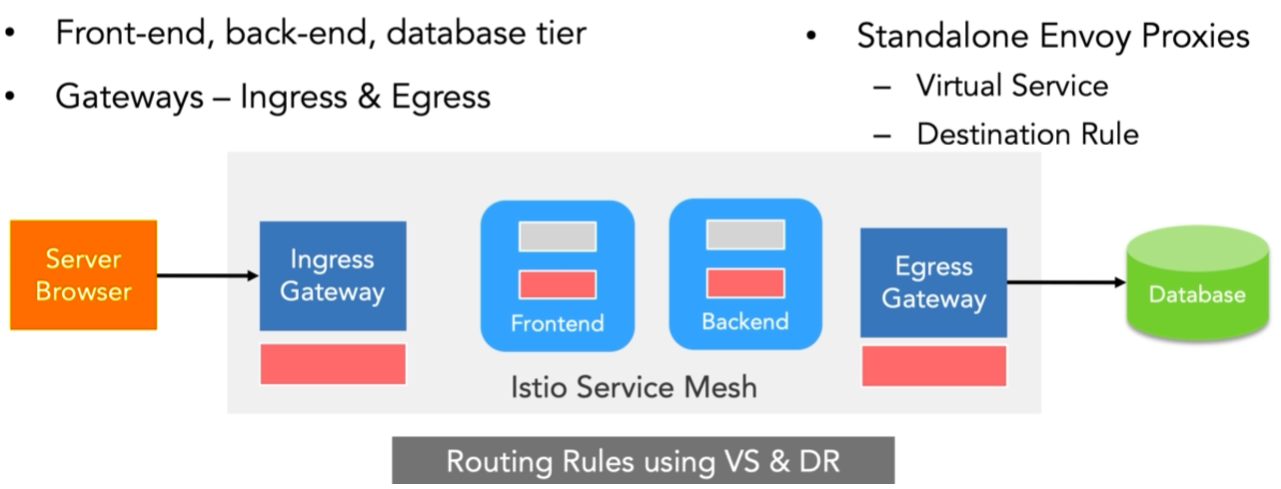
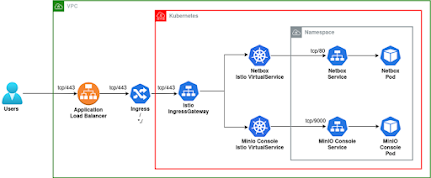
WAF
- https://www.intelligentdiscovery.io/controls/api/api-waf-integration
- https://docs.aws.amazon.com/apigateway/latest/developerguide/apigateway-control-access-aws-waf.html
- https://www.wafcharm.com/en/blog/aws-waf-supports-amazon-api-gateway/
- https://docs.aws.amazon.com/waf/latest/developerguide/getting-started.html
- https://docs.aws.amazon.com/waf/latest/developerguide/setting-up-waf.html
Load Balancer
- https://docs.aws.amazon.com/elasticloadbalancing/latest/application/create-listener.html
- https://aws.amazon.com/premiumsupport/knowledge-center/api-gateway-application-load-balancers/
OKTA
- https://awskarthik82.medium.com/part-3-securing-aws-api-gateway-using-jwt-authorizer-okta-jwt-access-token-cb2c9425b026
- https://github.com/okta/okta-jwt-verifier-java/blob/master/examples/quickstart/src/main/java/com/okta/jwt/example/ReadmeSnippets.java
- https://unbounded.io/securing-api-gateway-with-okta-serverless-framework-and-ssm-9e679af614e2
- https://github.com/okta/okta-oidc-js/commit/08789a57ac77977f7628bb2eb6351e9c280c482e#
- https://github.com/tom-smith-okta/node-lambda-oauth2-jwt-authorizer
- https://auth0.auth0.com/u/login/identifier?state=hKFo2SBmemVIb0Vna0tRdHV4OUFfT244OG0zM1JLdS1Ncl9wUKFur3VuaXZlcnNhbC1sb2dpbqN0aWTZIFZRNndzYy1iVW9sSmlmS0dPNjB5VWRabFNzZlJqeWlYo2NpZNkgekVZZnBvRnpVTUV6aWxoa0hpbGNXb05rckZmSjNoQUk
- Protect your API endpoints | Okta Developer
- okta-dev-57960638 - Authorization Server
- https://developer.okta.com/docs/reference/core-okta-api/
- https://developer.okta.com/docs/guides/validate-access-tokens/dotnet/main/#decoding-and-validating-the-access-token
- https://github.com/bgarlow/oktacar-lambda-authorizer
Lambda
- https://docs.aws.amazon.com/lambda/latest/dg/lambda-intro-execution-role.html
- https://docs.aws.amazon.com/lambda/latest/dg/configuration-envvars.html#configuration-envvars-config
- okta-api-center/lambda.md at master · tom-smith-okta/okta-api-center · GitHub
- GitHub - tom-smith-okta/node-lambda-oauth2-jwt-authorizer: OAuth 2.0 Bearer JWT Authorizer for AWS API Gateway
- Use API Gateway Lambda authorizers - Amazon API Gateway
- GitHub - aws-samples/openbanking-brazilian-auth-samples
- https://www.npmjs.com/package/@okta/jwt-verifier
- https://developer.okta.com/blog/2020/05/27/serverless-java-aws
API Gateway
- https://docs.aws.amazon.com/apigateway/latest/developerguide/configure-api-gateway-lambda-authorization-with-console.html
- https://github.com/tom-smith-okta/okta-api-center/blob/master/gateways/aws/lambda.md
- https://aws.amazon.com/blogs/security/use-aws-lambda-authorizers-with-a-third-party-identity-provider-to-secure-amazon-api-gateway-rest-apis/
- https://docs.aws.amazon.com/apigateway/latest/developerguide/api-gateway-caching.html
- Configure a Lambda authorizer using the API Gateway console - Amazon API Gateway
- https://docs.aws.amazon.com/apigateway/latest/developerguide/api-gateway-create-api-from-example.html
- https://docs.aws.amazon.com/apigateway/latest/developerguide/welcome.html
- https://aws.amazon.com/premiumsupport/knowledge-center/api-gateway-application-load-balancers/
- https://arpadt.com/articles/protect-alb-with-private-integration
- https://blog.developer.adobe.com/deploy-microservices-using-aws-ecs-fargate-and-api-gateway-1b5e71129338
- https://www.linkedin.com/pulse/generating-api-gateway-rest-endpoints-eks-alb-ingress-srinivasan/
- https://medium.com/swlh/aws-api-gateway-private-integration-with-http-api-and-a-vpc-link-602360a1cd84
Terraform
Extras
- https://jsonplaceholder.typicode.com/users
- https://jwt.io/
- How to easily setup Istio service mesh in AWS EKS (linkedin.com)
- https://www.eliasbrange.dev/posts/deploy-fastapi-on-aws-part-2-fargate-alb/
- https://www.linkedin.com/pulse/end-confusion-integrate-alb-api-gateway-faizan-weldon/